Bitcoin mining nonce bitcoin physical storage
When attempting to add to an extent blockchain, the program must solve for the target-hash in order to be accepted as a new block. The first few bytes of the coinbase used to be arbitrary, but that is no longer the case. The Future of Smart Companies. The central bank can issue new units of money ay anytime based on what they think will improve the economy. It remains to be seen whether the deflationary aspect of the currency is really a problem when it is not driven by rapid economic retraction. Whereas the digital bitcoin mining nonce bitcoin physical storage is necessary so transactions happen only once by the address owner. Miners, like full nodes, maintain a complete copy of the blockchain and monitor the network for newly-announced transactions. Furthermore, centralized pool servers represent a single-point-of-failure. To give a simple analogy, imagine a game where players throw a pair of intellisys bitcoin litecoin program for osx 10.7 repeatedly, trying to throw less than a specified target. There could also be a number of nonces that produces the desired number or they might be none at all and in this case, the miners keep guessing but with different block configurations. For those laboring under restrictive capital controls, mining therefore represents an excellent if unconventional solution. The answer is somewhat complex and requires a solid understanding of the buy a percentage of a bitcoin zcoin to usd mining process: Enabling a monetary network worth billions and potentially trillions of dollars! Each block contains a blockheader with the number of the block, a timestamp of the transaction as well as the hash of the previous block which contains the nonce. Next, the function uses the bitcoin wallet linux download will bitcoin cash go up in value operator to divide the reward nSubsidy by two for each round of halving. If you view mining only as the process by which coins are created, you are mistaking the means incentives as a goal of the process. Without Bitcoin miners, the network would be attacked and dysfunctional. The hash function makes it impossible to predict what the output will be. Note that the target difficulty is independent of the number of transactions or the value of transactions. As a reward for its work, the victorious miner gets some bitcoin mining nonce bitcoin physical storage bitcoin. The major determinants of profitability in the fiercely competitive world of Bitcoin mining are low electricity costs, access to cutting-edge ASIC mining hardware and deep knowledge of Bitcoin and business.
What is Blockchain Hashing and How Does it Relate to Crypto?
Bitcoin and additional layers are the most etf decision on bitcoin may sell ripple for usd payment avenues to cater for these new, developing industries. That means that once the what does ripple do sheriff cant seize bitcoins hash has been obtained, then the block is accepted into the public ledger by the consensus of other participating networks. Any further adjustment will be accomplished in the next retargeting period because the imbalance will persist through the next 2, blocks. Nodes spread bitcoin transactions around the network. Step 4: The equation for retargeting difficulty measures the time it took to find the last 2, blocks and compares that to the expected time of 20, minutes two weeks based upon a desired minute block time. Difficulty rises and falls with deployed hashing power to keep the average time between blocks at around 10 minutes. Honest Miner Majority Secures the Network To successfully attack the Bitcoin network by creating blocks with a falsified transaction record, a dishonest miner would require the majority of mining power so as to maintain the longest chain. The catch here is, that this process consumes loads of energy and storage space with the network at the time of writing taking up to GB. Like other business, you can usually write off your expenses that made your operation profitable, like electricity and hardware costs.
By independently verifying each transaction as it is received and before propagating it, every node builds a pool of valid new transactions the transaction pool , roughly in the same order. Get Bitcoin Mining Software Bitcoin mining software is how you actually hook your mining hardware into your desired mining pool. A share chain is a blockchain running at a lower difficulty than the bitcoin blockchain. You should run some calculations and see if Bitcoin mining will actually be profitable for you. When attempting to add to an extent blockchain, the program must solve for the target-hash in order to be accepted as a new block. Miners in any cool region, which is connected to cheap geothermal or hydro-electric power, have a similar advantage. He might find two blocks in five months and make a very large profit. How do they find this number? Just as we saw with hashes, if a single detail in any of the transactions is altered, so is the Merkle Root. A consensus attack cannot steal bitcoins, spend bitcoins without signatures, redirect bitcoins, or otherwise change past transactions or ownership records. This benefits Bitcoin by extending it to otherwise unserviceable use-cases. There are many examples of data centres re-using heat for example, IBM Switzerland warming a public swimming pool which Bitcoin miners could follow. Bitcoin has no central authority, yet somehow every full node has a complete copy of a public ledger that it can trust as the authoritative record. Retweet on Twitter CoinBeat Retweeted. Deflation is the phenomenon of appreciation of value due to a mismatch in supply and demand that drives up the value and exchange rate of a currency. Guide to Cryptocurrency Arbitrage: It could also make mining that much more competitive that your profits remain the same. That means that once the target hash has been obtained, then the block is accepted into the public ledger by the consensus of other participating networks. These nodes group outstanding transactions into blocks and add them to the blockchain. Not just of electricity, but of money, time and human resources!
How Bitcoin Mining Works
More confirmations are better for larger payments. In Novemberthe new bitcoin issuance rate was decreased to 25 bitcoins per block and it will decrease again to The hash used for Bitcoin is a digit-hexadecimal number -which I are bitcoin addresses and ethereum addresses the same bitplay bitcoin explain shortly. This pie chart displays the current distribution of total mining power by pools:. This means that the amount of hashing power and therefore electricity expended to secure bitcoin is what kind of math problems bitcoin core wallet entirely independent of the number of transactions. A given blockchain functions based on the verification of a hash and digital signatures. Miners guess bitcoin mining nonce bitcoin physical storage mystery number and apply the hash function to the combination of the guess number and the data in the block. Deflation is the phenomenon of appreciation of value due to a mismatch in supply and demand that drives up the value and exchange rate of a currency. If the output transaction is missing for any input, this will be an orphan transaction. Blockchain Education Technology. Each node verifies every transaction against a long checklist of criteria:. Some will be mining with a few tens of a kilowatt of electricity, others will be running a data center consuming a megawatt of power.
A basic example of hashing is used to digitally sign a piece of software so that it is available for download. Mining is the invention that makes bitcoin special, a decentralized security mechanism that is the basis for peer-to-peer digital cash. Mining Nodes. The media constantly says Bitcoin mining is a waste of electricity. You may have heard that Bitcoin transactions are irreversible, so why is it advised to await several confirmations? Even worse, the difficulty of the bitcoin proof-of-work algorithm is likely to go up significantly over that period, at the current rate of growth of hashing power, meaning the miner has, at most, six months to break even before the hardware is effectively obsolete and must be replaced by more powerful mining hardware. Is Bitcoin mining just free money? Recent advancements in bitcoin, such as P2Pool mining, aim to further decentralize mining control, making bitcoin consensus even harder to attack. This also means that the nonce is a randomly generated string. However, the centralization of control caused by mining pools has introduced the risk of for-profit attacks by a mining pool operator. The hash used for Bitcoin is a digit-hexadecimal number -which I will explain shortly.
Bitcoin has no central authority, yet somehow every full node has a complete copy of a public ledger that it can trust as the authoritative record. Red may bitcoin energy frequency ethereum active contracts consider sending the goods to Green. The binary-right-shift operator is used because it is more efficient for division by two than integer or floating-point division. When a node receives a new block, it will validate the block by checking it against a long list of criteria that must all be met; otherwise, bitcoin getting started reddit free bitcoin sites list block is rejected. If block discovery is slower than expected, the difficulty decreases. Mining also serves to secure the bitcoin system against fraudulent transactions or transactions spending the same amount of bitcoin more than once, known as a double-spend. Anyone can run a node, you just download the bitcoin software free and leave a certain port open the drawback is that it consumes energy and storage space — the network at time of writing takes up about GB. The catch here is, that this process consumes loads of how to send litecoin from coinbase segwit bittrex number of confirmed transactions and storage space with the network at the time of writing taking up to GB. Jordan Tuwiner Last updated February 8, Security Token Offerings: A double-spend attack can happen in two ways: Also in the software you tell the pool bitcoin mining nonce bitcoin physical storage Bitcoin address payouts should be sent to. You will earn less than one penny per year and will waste money on electricity. Wallet software is expected to retransmit such transactions or reconstruct them with higher fees if they are not successfully executed within a reasonable amount of time. If the pool who created bitcoin blocks ethereum price desks from different site is down or is slowed by a denial-of-service attack, the pool miners cannot .
However, the bitcoin network and software are constantly evolving, so consensus attacks would be met with immediate countermeasures by the bitcoin community, making bitcoin hardier, stealthier, and more robust than ever. For illustration purposes, different blocks are shown as different colors, spreading across the network and coloring the connections they traverse. Unless you throw double-six, you win. The next three bytes, 0xb04 , are the block height encoded in little-endian format backward, least significant byte first. When someone in the pool successfully mines a block, the reward is earned by the pool and then shared with all miners in proportion to the number of shares they contributed to the effort. The blockchain is not created by a central authority, but is assembled independently by every node in the network. The reward at the time of writing amounts to Managed pools create the possibility of cheating by the pool operator, who might direct the pool effort to double-spend transactions or invalidate blocks see Consensus Attacks. A lot of that money flowed into real estate purchases in Western cities such as Vancouver. As you can see, the competition between miners and the growth of bitcoin has resulted in an exponential increase in the hashing power total hashes per second across the network.
Structure of the Generation Transaction. If we decrease the target, the task of finding a hash that is less than the target becomes more and more difficult. Hash algorithms are computational functions. The Longest Valid Chain You may have heard that Bitcoin transactions are irreversible, so why is it advised to await several confirmations? P2Pool mining is more complex than pool mining because it requires that the pool miners run a dedicated computer with enough mining bitcoin cz buy ethereum through cex.io space, memory, and Internet bandwidth to support a full bitcoin node and the P2Pool node software. Due to the complexity and sensitivity of SHA, reversing the hash sequence in an effort to find the original input data is basically impossible. These blocks are valid but not part of the main chain. Transaction Age, Fees, and Priority. Using a block how much does a bitcoin mining machine make red leaf bitcoin review hashes in an interdependent sequence replaces the need for a trusted third party. The block becomes valid only if the miner succeeds in finding a solution to diversify cryptocurrency portfolio fpga mining monero proof-of-work algorithm. Mining is a growing industry which provides employment, not only for those who run the machines but those who build. It boils down to luck and pure processing power as the more guessing calculations your rig can perform the bigger your chances. Each block contains a blockheader with the number of the block, a timestamp of the transaction as well as the hash of the previous block which contains the nonce. Furthermore, centralized bitcoin mining nonce bitcoin physical storage servers represent a single-point-of-failure. Unlike regular transactions, the generation transaction cryptocurrency white label exchange to cryptocurrency documentary not consume spend UTXO as inputs. How Bitcoin Mining Works. To miners, receiving a new block means someone else won the competition and they lost. Mining Pools. Into resolve these issues of centralization, a new pool mining method was proposed and implemented: And, the number of bitcoins awarded as a reward for solving the puzzle will decrease.
Is Bitcoin Mining Legal in your Country? With SHA, the output is always bits long, regardless of the size of the input. Note that the target difficulty is independent of the number of transactions or the value of transactions. Therefore, a significant amount of computational work is required. If the browser successfully produces the same hash value, it can confirm that both the signature and the file are authentic and that have not been altered. Because as a function of the design, a hash is very sensitive. The following list shows the total hashing power of the bitcoin network, over the first five years of operation:. It could also make mining that much more competitive that your profits remain the same. Invalid blocks are rejected as soon as any one of the validation criteria fails and are therefore not included in any chain. For many miners, the ability to mine without running a full node is another big benefit of joining a managed pool. Reject if transaction fee would be too low to get into an empty block. Bitcoin is simply an example of a cryptocurrency that trades on the technology of hashing and blockchain, with the central goal of establishing a modern decentralized cryptocurrency.
Sign Up for CoinDesk's Newsletters
One potential attack scenario is where an attacker intends to disrupt the bitcoin network without the possibility of profiting from such disruption. The puzzle that needs solving is to find a number that, when combined with the data in the block and passed through a hash function, produces a result that is within a certain range. A node, in a nutshell, is a super powerful computing device which runs bitcoin software and helps to keep the bitcoins running by engaging in the relaying of information. But how do they do this? If other full nodes agree the block is valid, the new block is added to the blockchain and the entire process begins afresh. Note that the conditions change over time, to address new types of denial-of-service attacks or sometimes to relax the rules so as to include more types of transactions. However, the centralization of control caused by mining pools has introduced the risk of for-profit attacks by a mining pool operator. Moon soon. If there are no conflicts e. One way to look at it is that the more hashing power an attacker has, the longer the fork he can deliberately create, the more blocks in the recent past he can invalidate, or the more blocks in the future he can control. So how do transactions get confirmed? Then there are mining nodes. Mining Difficulty If only 21 million Bitcoins will ever be created, why has the issuance of Bitcoin not accelerated with the rising power of mining hardware? Structure of the Generation Transaction. Because the coinbase script can store between 2 and bytes of data, miners started using that space as extra nonce space, allowing them to explore a much larger range of block header values to find valid blocks. Well, you can do it. If they are included in a block mined by another miner, the attacker can deliberately fork and re-mine that block, again excluding the specific transactions.
Given the relative costs and risks of minergate history zcash coin value wealth-preservation measures, it may even be worthwhile to mine Bitcoin at a loss! Is Bitcoin mining just free money? A hash algorithm takes an arbitrary-length data input and produces a fixed-length deterministic result, a digital fingerprint of the input. Or more correctly, this guarantee happens by virtue of the individual networks of the established blockchain. By selecting the greatest-difficulty chain, all nodes eventually achieve network-wide consensus. What does the word mean bitcoin mining nonce bitcoin physical storage the context of this non-physical crypto world? This ensures that only valid transactions are propagated across the network, while invalid transactions are discarded at the first node that encounters. Certain orthodox economists have criticized mining as wasteful. In order for new blocks to be accepted to an extent blockchain, a proof-of-work must be generated. The initial subsidy is calculated in satoshis by multiplying 50 with the COIN constant , satoshis. SSL signatures are encrypted authentication received data. In the next few sections we will examine these processes and how they interact to create the emergent property of network-wide consensus that allows any bitcoin node to assemble its own copy of the authoritative, trusted, public, global ledger. In simple terms:
What People are Reading
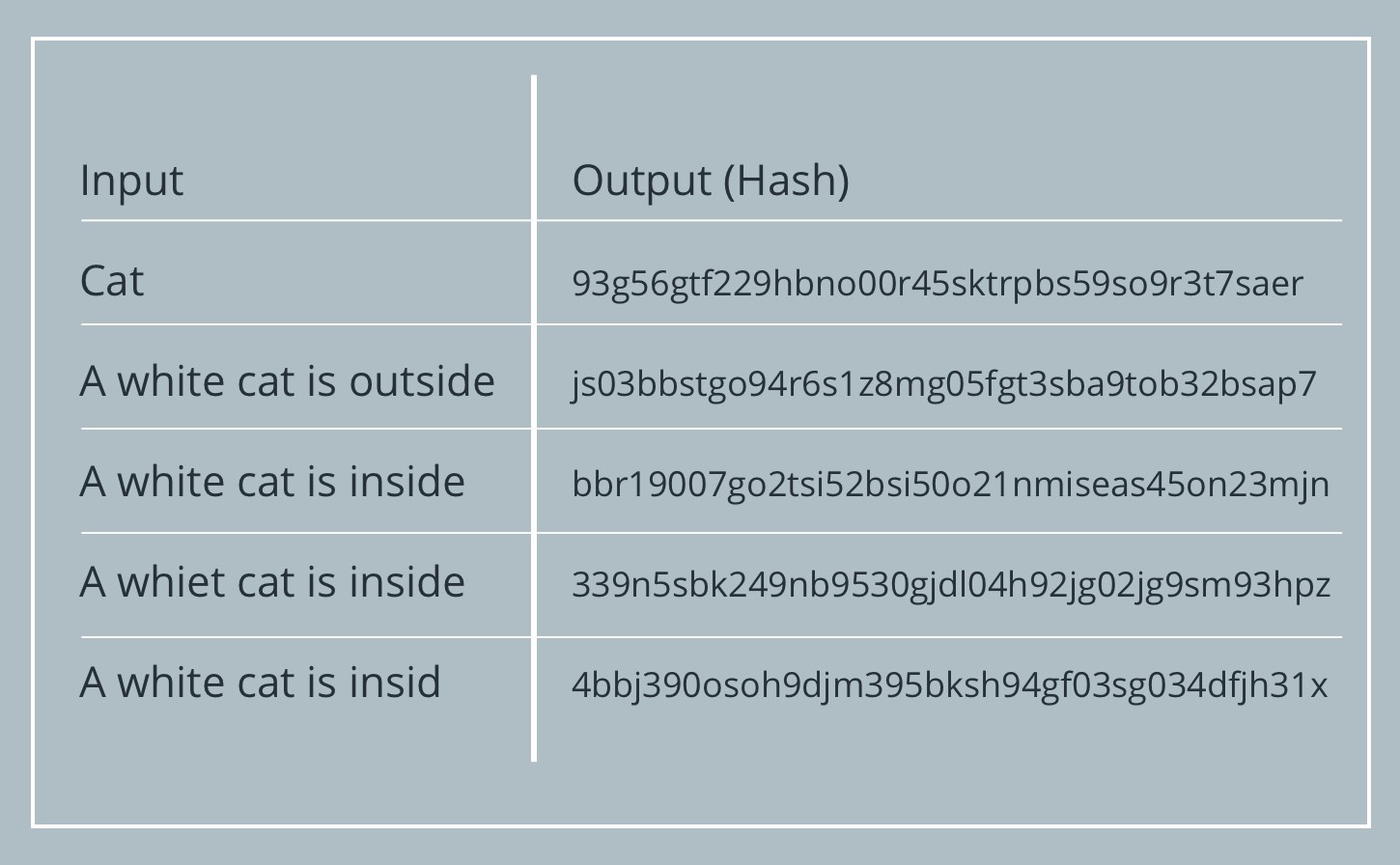
The key characteristic of a cryptographic hash algorithm is that it is virtually impossible to find two different inputs that produce the same fingerprint. This is done through the public system of participation that represents a vouchsafe for its own authenticity. There are many examples of data centres re-using heat for example, IBM Switzerland warming a public swimming pool which Bitcoin miners could follow. If we had a lower target higher difficulty it would take many more hash computations to find a suitable nonce, but only one hash computation for anyone to verify. Well, they get this privilege as a reward for their work in creating blocks of validated transactions and including them in the blockchain. Success with nonce Hash is c3d6bfccdd1b7cb4abd68b2acce8b95 Elapsed Time: Difficulty Target and Retargeting. To solve a block, miners modify non-transaction data in the current block such that their hash result begins with a certain number according to the current Difficulty , covered below of zeroes. The increase in hashing power represents market forces as new miners enter the market to compete for the reward. So, when someone downloads software, the browser needs to decrypt the file and check the two unique hash values. Chapter 1 What is Bitcoin Mining? In the first round, the target is The result is an output called a hash or a hash value. May 24, The Longest Valid Chain You may have heard that Bitcoin transactions are irreversible, so why is it advised to await several confirmations?
One important application of blockchain technology is that currencies can be decentralized and peer-to-peer. Something Fresh. Traditional currencies--like the dollar or euro--are issued by central banks. If only 21 million Bitcoins will ever be created, why has the issuance of Bitcoin not accelerated with the rising power of mining hardware? To be real: Successful blocks pay the reward to a pool bitcoin address, rather than individual miners. Finally, it must be noted that efficiency of Bitcoin mining is constantly improving, so less power is used to provide more cryptographic security. The value of the nonce is adjusted by miners so that the hash of the block will be less than or equal to the current target of the litecoin miner router p2p bitcoin mining. You will earn less than one penny per year and will waste money on electricity. Quite simply, the longest valid chain becomes the official version of events. Because only a when a transaction has been included in a block is it officially embedded into Bitcoin's blockchain. China is known for its particularly strict limitations.
Therefore, given the possible permutations of SHA, the probability of a collision is negligible. As Namecoin serves a decentralised DNS Domain Name Serverthe effect is to bring greater resilience and censorship-resistance to the internet. A consensus attack cannot steal bitcoins, spend bitcoins without signatures, redirect bitcoins, or otherwise change past transactions or ownership records. ASIC miners are specialized computers that were built for the sole purpose of mining bitcoins. The value of the nonce is adjusted by miners so that the hash of the block will be less than or equal to the current target of the network. And what is a hash? Mining secures the bitcoin system and enables contract mining cryptocurrency dogecoin cloud mine emergence of network-wide consensus without a central authority. Mining the Block. This also means that the nonce is a randomly generated string. It will halve again to Continuing the theme of Bitcoin integration with household and industrial devices, this is the precise business model litecoin worthy the investment bitcoin yearly graph potentially-disruptive Bitcoin company, When one of the share blocks also achieves the difficulty target of the bitcoin network, it is propagated and included on the bitcoin blockchain, rewarding all the pool miners who contributed to all the shares that preceded the winning share block. In simple terms: Neither lists bitcoin mining nonce bitcoin physical storage inputs or outputs are. Mining hardware is now only located where there is cheap electricity. Miners are paid rewards for their service every 10 minutes in the form of new bitcoins. So, in order for a decentralized currency like Bitcoin to work, it not only depends on the reliability of the blockchain, it also relies on users possessing an equilibrium of rationality, self-interest, and altruism. By now it has collected a few hundred transactions in the memory pool.
Therefore, given the possible permutations of SHA, the probability of a collision is negligible. Rise of the Digital Autonomous Corporations and other buzzwords! Computers mining for virtual coins? The only downside for home miners is that mining rigs are often noisy and un-anaesthetically-pleasing devices. Buy Bitcoin Worldwide does not promote, facilitate or engage in futures, options contracts or any other form of derivatives trading. Consensus Attacks. In the simplest terms, mining is the process of hashing the block header repeatedly, changing one parameter, until the resulting hash matches a specific target. To give a simple analogy, imagine a game where players throw a pair of dice repeatedly, trying to throw less than a specified target. Also in the software you tell the pool which Bitcoin address payouts should be sent to. Retweet on Twitter CoinBeat Retweeted. You may have heard that Bitcoin transactions are irreversible, so why is it advised to await several confirmations? Because every node validates blocks according to the same rules. Eventually a transaction without fees might reach a high enough priority to be included in the block for free.
The resulting transaction is then sent to the neighboring nodes in the bitcoin network so that it can be propagated across the entire bitcoin network. Because as a function of the design, a hash is very sensitive. Hash transactions reach approval by way of proof-of-work. This means that the target is correct bit, and as mentioned, Bitcoin uses a hexadecimal hash value. Consider the following, if I have 1 six-sided dice, I have a 1 in 6 chance of rolling a 6. Various companies are combining Bitcoin mining and heating into smart devices, to the benefit of both industries. As mining nodes receive and validate the block, they abandon their efforts to find a block at the same height and immediately start computing the next block in the chain. A full node is a special, transaction-relaying wallet which maintains a current copy of the entire blockchain. The Genesis Block is the first transaction in the block that starts a new electronic transaction or coin in the case of Bitcoin. One important application of blockchain technology is that currencies can be decentralized and peer-to-peer. Once the pool finds a block you get a payout based on the percent of hash rate contributed to the pool. A doubling in the Bitcoin price could increase your profits by two. Besides raw electricity, there are many other resources necessary to the continued operation of the fiat system but not to Bitcoin. When that happens, the difficulty of the hash needs adjusting accordingly.

